Blogs / Cloud Security
How to Detect & Prevent DDoS Attacks in Cloud Computing
By
Sibin Vincent
Posted: April 18th, 2024
• 8 minutes and 50 seconds
In this article, you will learn:

DDoS (Distributed Denial of Service) attacks aren't hypothetical – they're a growing threat with massive consequences. A single attack can cripple operations for hours, causing significant financial loss and reputational damage.
Remember when GitHub got hit in 2018? A massive DDoS attack, the largest recorded at the time, took their platform down for an impactful eight minutes. A staggering amount of data was sent to GitHub’s servers during the peak of the attack (9.35 terabits per second). This wasn't an isolated incident. Just think back to the infamous 2016 attack on DNS provider Dyn and the 2000 Mafiaboy incident, demonstrating the persistent threat of DDoS attacks over the years.
The threat doesn't stop there - major corporations like Microsoft, AWS, and Google have faced these attacks constantly. Fortunately, these tech giants have strong cloud-based security solutions that can effectively neutralize DDoS threats. Recently, Google successfully defended against a record-breaking attack, proving the importance of robust defenses.
What is DDoS (Distributed Denial of Service) Attack?
A DDoS (Distributed Denial-of-Service) attack is a cyber attack aimed at disrupting the regular operation of a website or online service. It is conducted by flooding the target server and network with more requests than it can handle. The rush of fake requests weakens the system's ability to respond to its genuine user requests, preventing customers from accessing the targeted business's services. In severe cases, the website can completely crash, causing outages that can last for hours.
Consider a scenario during a major online sale where hackers exploit thousands of hijacked computers to flood the store's website with fake requests. If the online store is usually capable of processing 100 orders per second, the DDoS attack just needs to flood the system with 101 fake orders per second to entirely block the genuine customers. This crowds the site, causing it to crash or become extremely slow. As a result, genuine shoppers trying to buy items will not be able to access the site, resulting in lost sales and frustration.
What are the common types of DDoS attacks?
DDoS attacks come in various forms, each targeting a different vulnerability in a system's defenses. Here, we break down these to help you understand their attack mechanisms and potential impacts.
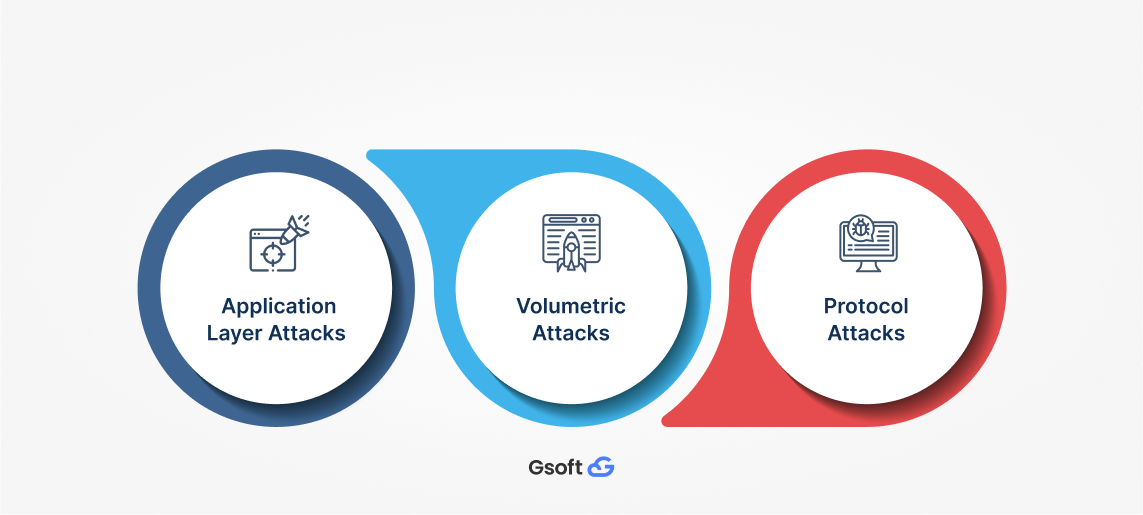
-
Application Layer Attacks:
Application layer attacks are less common but more advanced, focusing on specific parts of an application. They aim to exploit weaknesses in particular application services rather than overwhelming the entire network. Detecting and stopping these attacks can be hard because they look like normal traffic, making it tricky to tell the difference between real and fake requests. Some examples of these attacks include:
- HTTP Floods: This involves sending a huge number of requests to a website, making it difficult for the server to handle the incoming traffic.
- DNS Query Floods: Here, the attacker overloads a DNS (Domain Name System) server with too many requests, interrupting its job of translating domain names into IP addresses. This makes it hard to find the right IP addresses.
- Targeting Login Pages: Attacking login pages involves flooding the server with too many login attempts. This blocks the real users from logging in.
-
Volumetric Attacks:
Volumetric Attacks are the most common type of DDoS attack, aiming to flood the target system with a massive amount of junk data. This overwhelms its bandwidth and causes a crash, making applications or services unavailable to users. These attacks are based on Brute Force techniques that flood the target with data packets to consume bandwidth and system resources. Volumetric Attacks, also referred to as Network floods, come in various forms, including UDP floods (UDP reflection attacks) and ICMP (Internet Control Message Protocol) floods.
- UDP Floods: In a UDP (User Datagram Protocol) flood attack, the attacker sends a flood of User Datagram Protocol (UDP) packets to the target system. The attackers can use Reflection Techniques, bouncing the packets off other vulnerable servers or devices before reaching the target, which makes the attack harder to stop.
- ICMP Floods: In an ICMP (Internet Control Message Protocol) flood attack, the attacker sends a flood of Internet Control Message Protocol (ICMP) packets to the target system. This overloads the system with messages, consuming its resources and causing it to become unresponsive to real traffic.
-
Protocol Attacks:
A protocol attack is a type of cyberattack that aims to exhaust the resources of a server or its networking systems, such as firewalls, routing engines, or load balancers. Protocol attacks exploit weaknesses in the established rules or communication protocols, which govern how devices communicate on a network by sending invalid messages or incomplete requests.
The most common type is the SYN flood. In this attack, the attacker floods the target server with tons of fake connection requests, which never result in a full connection. These requests overwhelm the server, draining its resources as it waits for the responses queue. This can eventually crash the server or block real users from getting the service.
As businesses are increasingly relying on cloud-based applications and systems to run their operations, a critical question emerges: how can DDoS attacks be prevented from disrupting operations?
How Does a DDoS Attack Work?
DDoS attacks operate through a network of compromised devices, known as botnets. This device network floods a target system with a huge amount of traffic. The aim is to consume the target's resources, such as bandwidth, processing power, or memory, to the point where genuine users can no longer access the service. This attack typically consists of three main stages:
-
Botnet Formation:
To form a botnet, attackers spread malware that infects a large number of computers or devices. These devices may include traditional computers and smartphones, as well as internet-connected gadgets like cameras or thermostats. Once hacked, these devices are grouped into a network controlled by the attacker.
-
Coordinated Attack:
At this stage, the attacker instructs the botnet to send a massive volume of requests or data packets to the target system. This can be done in various ways. For instance, they may send different types of connection requests to drain the server's resources, making it unresponsive. These requests often appear authentic, making it difficult to differentiate them from normal traffic. Similarly, the attacker floods the target system with an enormous volume of data packets to exhaust the system's bandwidth and processing power.
-
Denial of Services:
The sudden spike in website traffic overwhelms the target's resources, leading to a slowdown or complete halt in operations. This makes the website or service inaccessible to users, resulting in a denial of service and interrupting the normal operations of the targeted business.
How to know if you are under a DDoS attack
The most apparent indicators of a DDoS attack include an unusually large volume of traffic from single IP addresses, sudden slowdowns of websites and applications, and unusual traffic patterns occurring at predictable intervals. The nature of DDoS attacks is constantly evolving, and detecting their signs early is important to minimize their impact. Below are key indicators that can help you identify if your system is under a DDoS attack.
-
Sudden Performance Issues
If your website or application experiences sudden slowdowns, intermittent outages, or becomes completely inaccessible, it could be a sign of a DDoS attack.
-
Unusual Traffic Patterns
Is a specific page on your website getting overloaded with requests, even though it's not that much popular? Or if traffic arrives in consistent bursts at predictable intervals? These patterns may indicate automated bot activity associated with a DDoS attack.
-
Traffic from Single IP Addresses
An unusually large volume of traffic originating from a single IP address or IP range might be a red flag. DDoS attackers often use botnets to amplify their attacks, so traffic from a single source could indicate coordinated malicious activity.
Effective Ways to Mitigate DDoS Attacks in the Cloud

-
Implement Rate Limiting
Rate limiting restricts traffic volume hitting a network or server. It enforces predefined limits on traffic volume within specific timeframes across multiple network layers—network, application, and even DNS. When these limits are reached, excess traffic is either discarded (blocked) or throttled (slowed down) to prevent overload. This targeted control effectively defends against DDoS attacks and API abuse, strengthening the resilience of critical system components.
-
Reduce Attack Surface
Attack surface refers to all the points, or potential entryways, through which an attacker could gain access to a system or network. This includes software vulnerabilities, open ports, user permissions, and any other weak spots that could be exploited. So, attack surface reduction involves taking proactive measures to minimize these vulnerabilities and strengthen the overall security of the system or network. Some of the methods you can include in your attack surface reduction strategies include:
- Network Segmentation: Divide and distribute assets within your network to increase attack complexity and system resilience. By segregating web servers into public subnets and database servers into private subnets and restricting access between them, you create barriers that make it harder for attackers to target critical assets.
- Geographical Restrictions: Geo-restrictions can be a helpful tool to limit exposure to potential DDoS attackers. By restricting traffic from regions with a lower volume of legitimate users, you can decrease the likelihood of attacks originating from those areas. For example, if your business primarily operates in the United States and you notice a high volume of DDoS attacks originating from certain countries in Asia with minimal legitimate user activity, you can implement geo-restrictions to block traffic from those regions. By doing so, you reduce the potential attack surface by limiting exposure to areas where attackers are more likely to originate from.
- Load Balancer Protection: Employ load balancers to shield web servers and computational resources from direct exposure to the internet. By directing incoming traffic through load balancers, you can evenly distribute the load and mitigate the impact of DDoS attacks targeting individual servers.
- Clean Application/Website: Regularly audit and optimize your application or website to remove any unnecessary services, features, or legacy systems/processes. This makes it much harder for attackers to find a chance and launch a DDoS attack.
-
Execute Content Delivery Networks (CDN)
Content Delivery Networks distribute your website content across multiple locations, reducing strain on individual servers. As a defense against DDoS attacks, CDN offers several advantages:
- Distribute incoming traffic across geographically dispersed servers, preventing overload on any single server during DDoS attacks.
- Dynamically scale resources to accommodate fluctuations in traffic volume, minimizing the impact of DDoS attacks on website performance.
- Employ sophisticated load-balancing algorithms to evenly distribute traffic, mitigating the risk of server overload and strengthening resilience against DDoS attacks.
- By serving cached copies of the content from edge locations, CDNs significantly decrease the number of requests reaching the origin server, lessening the strain on the origin server during an attack.
- Users can still access cached content from nearby edge locations even if the origin server is under attack, ensuring a smoother user experience and helping maintain website availability during DDoS attempts.
- Many CDNs offer built-in DDoS protection services that monitor and mitigate malicious traffic in real time to ensure uninterrupted service availability.
-
Deploy Web Application Firewall
Deploying Web Application Firewalls (WAFs) is a critical measure in defending against DDoS attacks, particularly those targeting the application layer. WAFs provide a frontline defense against malicious traffic seeking to exploit vulnerabilities within applications. The main advantages of deploying WAFs include the following:
- Effectively prevent attacks such as SQL injection and cross-site scripting, which aim to exploit vulnerabilities in web applications.
- Allow for the creation of customized rules to mitigate illegitimate requests, including those disguised as genuine traffic or originating from malicious IPs or unexpected geographies.
- WAF solutions like AppTrana offer round-the-clock monitoring by security experts, enabling the identification and blocking of fake traffic surges without disrupting genuine traffic.
- Mitigate DDoS attacks by intercepting and halting malicious traffic before it reaches the origin server, preventing server overload and reducing the risk of service disruption.
- WAFs can be deployed in various configurations, including network-based, host-based, and cloud-based, providing organizations with flexibility in implementing their defense strategies.
-
Implement Real-time Threat Monitoring
Real-time Threat Monitoring allows you to continuously analyze network traffic patterns and unusual activities. This may include sudden spikes in traffic volume, anomalous traffic patterns, or suspicious requests. This allows you to defend against DDoS attacks by quickly mitigating the attack or implementing pre-defined mitigation strategies. Real-Time Threat Monitoring helps to prevent DDoS attacks in the following ways:
- Advanced monitoring tools go beyond simple anomaly detection. They use sophisticated algorithms to identify suspicious activity, including malicious requests, protocols, or specific IP blocks attempting to overwhelm your network, ensuring your defenses remain effective against evolving DDoS tactics.
- When real-time monitoring detects a potential threat, it triggers immediate alerts. These alerts can be routed to your security team, Security Operations Centers (SOCs), or even specialized DDoS mitigation services, allowing for a quick and coordinated response to neutralize the attack.
-
Employ Bot Managers
Bot managers utilize various techniques to differentiate between human users and bots, as well as behavioral analysis comparing user behavior to historical data. Upon identifying malicious bots, bot managers can take proactive measures such as redirecting them to different pages or blocking their access to web resources altogether. Conversely, good bots may be added to allow lists, while further behavioral analysis helps distinguish between good and bad bots.
Bot managers utilize various methods to identify bots:
- JavaScript Challenges: These challenges test a user's ability to execute JavaScript code, a skill beyond most simple bots. If a user fails this test, they're likely a bot.
- CAPTCHA Challenges: These visual puzzles are designed to be difficult for bots to solve, further differentiating humans from automated programs.
- Behavioral Analysis: By analyzing user behavior patterns, bot managers can identify anomalies. This may involve comparing a user's actions to historical data on legitimate user behavior. A large collection of past user interactions is crucial for effective behavioral analysis.
What is the impact of a DDoS Attack?
Unlike other cyber-attacks, DDoS attacks usually don't involve data theft, destruction, or corruption. Instead, they cause harm by making it impossible for organizations to use essential systems and services, leading to high recovery costs. Banks, media companies, governments, and other large organizations are common targets due to the significant disruption these attacks cause.
- Companies that heavily depend on their online presence, like e-commerce and SaaS firms, suffer significant financial losses and operational disruptions due to these attacks.
- Recovery from DDoS attacks often involves substantial costs, including investments in cybersecurity measures and potential damage to brand reputation.
- Mitigating DDoS attacks is challenging due to the distributed nature of attackers, who utilize networks of compromised devices scattered across the globe.
- The evolving sophistication of DDoS attacks poses an increasing threat to businesses over time, emphasizing the importance of proactive cybersecurity measures.
Secure Your Cloud Infrastructure with Gsoft Security Services
DDoS attacks are becoming increasingly common, posing a significant threat to any organization's online presence. The consequences of not being prepared can be devastating, leading to months of damage control and reputational harm.
Gsoft Cloud can help you protect your business with the best cloud security services and ensure a seamless online experience for your customers with our customized DDoS protection strategies. Here's how:
- Comprehensive security expertise capable of designing and implementing robust security measures for your cloud infrastructure.
- 24/7 Monitoring of your systems for quick detection and response to potential threats.
- Advanced DDoS Protection for your application by leveraging the power of AWS Edge Services, including Amazon CloudFront, AWS WAF, Amazon Route 53, and AWS Shield.
- Scalable DDoS protection solutions that are designed to adapt to your business as it grows.
Schedule a free consultation with Gsoft Cloud’s security specialists today to discuss how we can protect your organization from DDoS attacks!
FAQs
Q:
What are the benefits of using cloud-based DDoS protection?
- DDoS attacks can hit with immense volumes of traffic. Cloud-based DDoS protection services can easily scale up or down to meet the ever-changing demands of your traffic.
- Cloud providers have dedicated security teams constantly monitoring and updating their DDoS mitigation strategies. These specialists can react quickly to new threats and deploy automated countermeasures.
- Cloud-based DDoS protection uses a geographically distributed network of servers that can absorb and filter the traffic before it reaches your website or application.
- Cloud-based DDoS protection is constantly active, monitoring your traffic 24/7 for suspicious activity. This ensures you're protected even outside of regular business hours.
Q:
What should I do if my cloud environment is under a DDoS attack?
Follow the below steps to mitigate the impact and restore normal operations when you recognize that your cloud environment is under a DDoS attack:
- If your cloud service provider offers DDoS protection services, activate them immediately to mitigate the attack.
- Inform your cloud service provider about the ongoing DDoS attack as soon as possible to handle the situation effectively.
- Use network monitoring tools to closely monitor incoming traffic and identify patterns associated with the DDoS attack.
- If feasible, adjust firewall rules to block traffic from suspicious IP addresses or implement rate limiting to reduce the impact of the attack on your cloud environment.
- Keep stakeholders, including customers, partners, and internal teams, informed about the situation and the steps being taken to mitigate the DDoS attack.
Q:
Can DDoS attacks be completely prevented?
DDoS attacks exploit vulnerabilities in network infrastructure and overwhelm systems with massive amounts of traffic, making them difficult to stop entirely. Attackers develop new methods constantly, the distributed nature of the attack makes it hard to trace and launching them doesn't require high technical skills. However, proactive measures such as deploying DDoS protection solutions, implementing network redundancy, and having robust incident response plans in place can significantly reduce the risk and mitigate the impact of DDoS attacks.
Q:
What are some common targets of DDoS attacks in cloud computing?
Common targets of DDoS attacks in cloud computing include websites, web applications, APIs (Application Programming Interfaces), online gaming platforms, and other cloud-based services that are critical to businesses and organizations.
Q:
Are there any legal or regulatory implications of DDoS attacks in cloud computing?
Depending on the nature of the attack and the industry regulations applicable to the affected organization, DDoS attacks in cloud computing may have legal and regulatory implications, particularly regarding data protection, privacy, and compliance requirements.
Q:
How are DDoS attacks mitigated in cloud computing environments?
Cloud service providers offer robust DDoS protection services that go beyond basic firewalls to safeguard your online presence. These services employ a multi-layered approach to detect, filter, and mitigate DDoS attacks, ensuring business continuity for their customers. Some of the key mitigation techniques include:
- Traffic filtering and analysis that offers Advanced algorithms that constantly analyze incoming traffic patterns.
- Rate Limiting to Limit the rate of incoming traffic, preventing overwhelming floods of requests from reaching target resources.
- Distributed cloud infrastructure across multiple geographic regions, allowing providers to reroute traffic away from affected regions during DDoS attacks.
- Real-time monitoring systems that continuously monitor network traffic and infrastructure health.
Q:
What should businesses consider when choosing a cloud service provider in terms of DDoS protection?
When selecting a cloud service provider, businesses should consider factors such as the provider's track record in mitigating DDoS attacks, the availability of DDoS protection services, the scalability of the provider's infrastructure, and the provider's transparency and communication during security incidents.


Get Know More About Our Services and Products
Reach to us if you have any queries on any of our products or Services.











